This portfolio documents my ability to write functional code, user and developer documentation and respond to pull requests.
Overview
Task Book is a desktop to-do list application. It is a GUI app but most of its user interactions happen in the Command Line Interface (CLI).
It is targeted at helping busy students manage their daily tasks
by keeping track of their to-do things, approaching deadlines and categorise them in an orderly manner.
Furthermore, Task Book allows you to set milestones for big projects so that you can finish them manageably on time.
If you can type fast, Task Book can manage your tasks faster than traditional paper notebooks or a mobile application.
Summary of contributions
Here is an overview of what I have done to support my team in achieving the final goal of our project.
-
Code contributions: tracked by Reposense
-
Main feature implemented: Allows students to add tasks into the
Task Book-
What it does: Adds a new task with its title, description, priority level and expected hours of completion
-
Justification: This is a core feature that serves the main purpose of
Task Bookand lays the foundation for other features to be built upon -
Highlights: Written model stubs and applied equivalence partitioning for unit-testing the feature to ensure sufficient coverage for the feature
-
-
Other minor enhancements:
-
Feature that allows students to complete existing tasks in the
Task Book-
What it does: Strikes off an incomplete task
-
Justification: Another crucial feature that allows students to focus on incomplete tasks and also track productivity
-
-
Feature that allows students to track their productivity
-
What it does: Calculates the average productivity for all the completed tasks
-
Justification: Helps students be more aware of their productivity rate
-
-
Modified code to follow software engineering principles such as Open-Closed Principle (OCP) over here and there
-
Beautified the User Interface (UI) to be more user-friendly (Pull request #63)
-
-
Other contributions:
-
Project management:
-
Set up the organization repository and its issue tracker
-
Closes milestones and tags repository biweekly
-
Managed releases
v1.1-v1.4(4 releases) on GitHub -
Added issue labels and assigned milestones to the team’s pull requests
-
Opened issues #7, #8, #22 to describe user stories of the product as well as to break down user stories into smaller tasks e.g. #39, #40
-
-
Documentation:
-
Wrote the use cases and user stories for other feature enhancements, as well
-
Drawn architecture and sequence diagrams to further substantiate how the feature is developed
-
-
Community:
-
Contributions to the User Guide
The following showcases my ability to write user documentation for add task, complete task,
and locking/unlocking the |
Adding a task: add
Adds a task with its title, description, priority level (low, medium, high) and the number of hours (positive integers only) expected
to complete this task, to the Task Book
|
Module code is an optional input. |
|
Tasks with similar deadline, title and module code are considered duplicate.
If a duplicate task is added, Task Book will give an error message: However, if the original task has no module code, you are allowed to add a similar task with a new module code. |
Format: add t/TITLE d/DESCRIPTION p/PRIORITY h/HOURS [c/MODULE_CODE]
Examples:
-
add t/Complete 2113 Tutorial d/with code done p/high h/1 -
add t/Complete 2113 Tutorial d/with code done p/high h/1 c/CS2113
Complete a task: complete
Complete a task in the Task Book by providing its index and the actual number of hours taken to complete the task
Format: complete i/INDEX h/HOURS_TO_COMPLETE
|
You are not allowed to complete a task in less than 1 hour! |
| If it takes more than 1 day to complete the task, it is recommended to set milestones for it. |
Examples:
-
complete i/1 h/2
Lock Task Book [coming in v2.0]
Task Book will be password-protected to ward off intruders.
Format: lock
Unlock Task Book [coming in v2.0]
Task Book can be unlocked so that authenticated students can log into the Task Book to access sensitive information.
Format: unlock PASSWORD
Contributions to the Developer Guide
The following showcases my ability to write use cases for add task, complete task,
developer documentation for locking |
Use case: Add new task
MSS
-
Student selects the deadline for a task
-
TB updates the selected date
-
Student requests to add a new task with some details
-
TB checks for the validity of command and adds the task to the list
Use case ends.
Extensions
-
3a. Student did not enter one or more compulsory input(s) for the task
-
3a1. TB tells student that input(s) is/are empty
Use case ends.
-
-
3b. Student enters a duplicated task
-
3b1. TB shows that task already exists in TB
Use case ends.
-
Use case: Complete task
MSS
-
Student selects the date of completed task
-
TB updates the selected date
-
Student requests to complete the task
-
TB checks for its validity and completes the task in TB
Use case ends.
Extensions
-
3a. Student attempts to complete the task in less than 1 hour
-
3a1. TB requests for student to enter a more suitable number of hour(s)
Use case resumes at step 4.
-
-
3a. Student wants to complete a completed task
-
3a1. TB gives an error to show that task is completed already
Use case ends.
-
Locking/Unlocking Task Book feature [coming in v2.0]
Proposed Implementation
To ensure encryption keys are both sufficiently random and hard to brute force,
we will use standard password-based encryption (PBE) key derivation methods.
When the student uses Task Book for the first time, he or she will be requested to enter a new password.
Since password recovery methods may not be implemented, this password must be easy to remember by the student.
Along with the password text provided by the student, a salt is appended to produce a hash (Figure below).
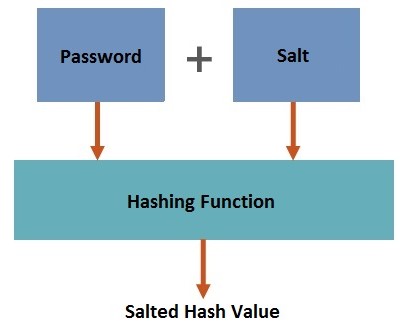
An AES or DES encryption key is thus derived from this process. To unlock the Task Book, the same salt is appended to the password provided to generate the decryption key.
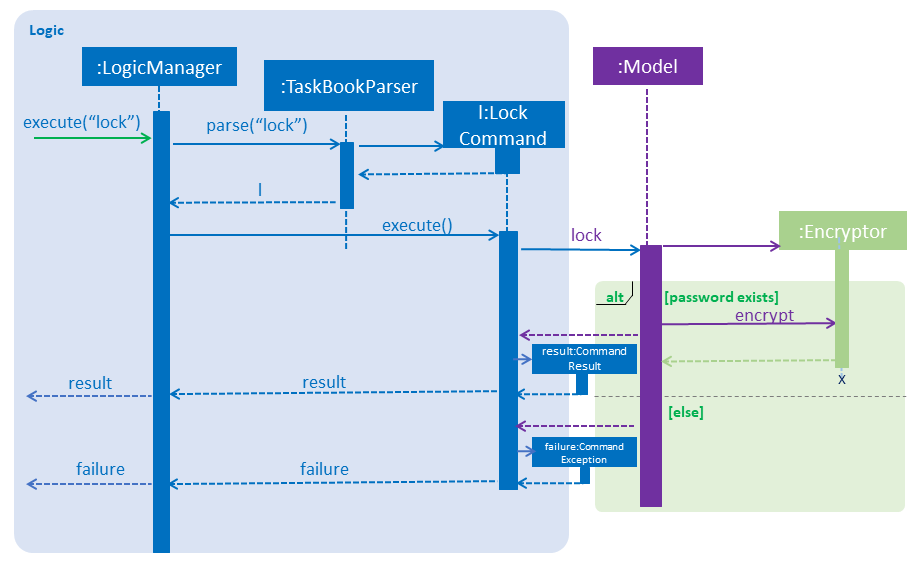
In the Sequence Diagram, these are the interactions within the Logic component for the execute("lock") API call (Figure below):
-
Logicparses the command and returns the LockCommand. -
During the command execution,
Modelchecks whether a password has been set. -
If so,
Encryptorwill encrypttaskbook.xmlfile so the Task Book cannot be seen by anyone without the password. -
Else, a
CommandExceptionis returned to prompt the user to set a password.
Design Considerations
There are a few ways to implement the password encryption for our product.
However, each method has its strengths and weaknesses. We will be explaining why we chose this particular implementation design.
Aspect: Online password authentication
-
Alternative 1: Offline password authentication
-
Pros: Simple and efficient method to log into Task Book with a lower risk of data breach
-
If student has set a complex password, it will be harder to hack into Task Book
-
-
Cons: Possible data loss if student’s password is forgotten
-
-
Alternative 2: Connect student logging session to an online authentication system
-
Pros: Allows students to reset their password, if forgotten
-
Cons: Extra step to connect to the internet and send hashed password to verify with the database. Additional space is also required in database to store users and their passwords securely.
-
Appendix A: Adding a task
-
Select a particular date
-
Select the date using the
selectcommand, or the date-picker in the UI. -
Test case:
select 11/11/2018
Expected: Tasks with the similar deadline are listed. Timestamp in the status bar is updated.
-
-
Add a task with title, description, priority and expected number of hours entered.
-
Test case:
add t/Do project portfolio d/convert to pdf format p/high h/3 c/CS2101
Expected: A task will be added to the list, together with the other tasks with the same deadline. -
Other incorrect add commands:
addoradd t/ d/ p/ h/with compulsory fields not entered oradd t/Do coding d/very fun p/midhigh h/1with invalid priority level.
-
Saving data
-
Dealing with missing/corrupted data files
-
If the file is corrupted due to illegal values in the data
-
Go to
data/taskbook.xmland delete the file
-
-
If the file is missing:
-
The filename may be incorrect, i.e. not
taskbook.xml, or -
taskbook.xmlmay not be in the/datafolder
-
-
Appendix B: Non Functional Requirements
Here are some conditions that are not explicitly stated in the features that Task Book provides, but are crucial features that allow users to operate the system functionally.
-
Should work on any mainstream OS as long as it has Java
9or higher installed. -
Should be able to respond within 2 seconds.
-
A user with above average typing speed for regular English text (i.e. not code, not system admin commands) should be able to accomplish most of the tasks faster using commands than using the mouse.
-
Will be offered free for students.
-
Not built to contain sensitive information due to lack of password protection.
-
Tasks dated as far as 10 years ago may be difficult to retrieve, unless data is backed up in the cloud storage.